| <!DOCTYPE html> | |
| <html lang="en-GB" prefix="og: http://ogp.me/ns# fb: http://ogp.me/ns/fb#" class="no-js"> | |
| <head> | |
| <meta charset="UTF-8"> | |
| <meta name="viewport" content="width=device-width"> | |
| <link rel="profile" href="https://gmpg.org/xfn/11"> | |
| <link rel="pingback" href="https://www.benthamsgaze.org/xmlrpc.php"> | |
| <!--[if lt IE 9]> | |
| <script src="https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/js/html5.js?ver=3.7.0"></script> | |
| <![endif]--> | |
| <script>(function(html){html.className = html.className.replace(/\bno-js\b/,'js')})(document.documentElement);</script> | |
| <title>Do you know what you’re paying for? How contactless cards are still vulnerable to relay attack – Bentham’s Gaze</title> | |
| <meta name='robots' content='max-image-preview:large' /> | |
| <link rel='dns-prefetch' href='//s.w.org' /> | |
| <link href='https://fonts.gstatic.com' crossorigin rel='preconnect' /> | |
| <link rel="alternate" type="application/rss+xml" title="Bentham’s Gaze » Feed" href="https://www.benthamsgaze.org/feed/" /> | |
| <link rel="alternate" type="application/rss+xml" title="Bentham’s Gaze » Comments Feed" href="https://www.benthamsgaze.org/comments/feed/" /> | |
| <link rel="alternate" type="application/rss+xml" title="Bentham’s Gaze » Do you know what you’re paying for? How contactless cards are still vulnerable to relay attack Comments Feed" href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/feed/" /> | |
| <script> | |
| window._wpemojiSettings = {"baseUrl":"https:\/\/s.w.org\/images\/core\/emoji\/13.0.1\/72x72\/","ext":".png","svgUrl":"https:\/\/s.w.org\/images\/core\/emoji\/13.0.1\/svg\/","svgExt":".svg","source":{"concatemoji":"https:\/\/www.benthamsgaze.org\/wp-includes\/js\/wp-emoji-release.min.js?ver=5.7.1"}}; | |
| !function(e,a,t){var n,r,o,i=a.createElement("canvas"),p=i.getContext&&i.getContext("2d");function s(e,t){var a=String.fromCharCode;p.clearRect(0,0,i.width,i.height),p.fillText(a.apply(this,e),0,0);e=i.toDataURL();return p.clearRect(0,0,i.width,i.height),p.fillText(a.apply(this,t),0,0),e===i.toDataURL()}function c(e){var t=a.createElement("script");t.src=e,t.defer=t.type="text/javascript",a.getElementsByTagName("head")[0].appendChild(t)}for(o=Array("flag","emoji"),t.supports={everything:!0,everythingExceptFlag:!0},r=0;r<o.length;r++)t.supports[o[r]]=function(e){if(!p||!p.fillText)return!1;switch(p.textBaseline="top",p.font="600 32px Arial",e){case"flag":return s([127987,65039,8205,9895,65039],[127987,65039,8203,9895,65039])?!1:!s([55356,56826,55356,56819],[55356,56826,8203,55356,56819])&&!s([55356,57332,56128,56423,56128,56418,56128,56421,56128,56430,56128,56423,56128,56447],[55356,57332,8203,56128,56423,8203,56128,56418,8203,56128,56421,8203,56128,56430,8203,56128,56423,8203,56128,56447]);case"emoji":return!s([55357,56424,8205,55356,57212],[55357,56424,8203,55356,57212])}return!1}(o[r]),t.supports.everything=t.supports.everything&&t.supports[o[r]],"flag"!==o[r]&&(t.supports.everythingExceptFlag=t.supports.everythingExceptFlag&&t.supports[o[r]]);t.supports.everythingExceptFlag=t.supports.everythingExceptFlag&&!t.supports.flag,t.DOMReady=!1,t.readyCallback=function(){t.DOMReady=!0},t.supports.everything||(n=function(){t.readyCallback()},a.addEventListener?(a.addEventListener("DOMContentLoaded",n,!1),e.addEventListener("load",n,!1)):(e.attachEvent("onload",n),a.attachEvent("onreadystatechange",function(){"complete"===a.readyState&&t.readyCallback()})),(n=t.source||{}).concatemoji?c(n.concatemoji):n.wpemoji&&n.twemoji&&(c(n.twemoji),c(n.wpemoji)))}(window,document,window._wpemojiSettings); | |
| </script> | |
| <style> | |
| img.wp-smiley, | |
| img.emoji { | |
| display: inline !important; | |
| border: none !important; | |
| box-shadow: none !important; | |
| height: 1em !important; | |
| width: 1em !important; | |
| margin: 0 .07em !important; | |
| vertical-align: -0.1em !important; | |
| background: none !important; | |
| padding: 0 !important; | |
| } | |
| </style> | |
| <link rel='stylesheet' id='wp-block-library-css' href='https://www.benthamsgaze.org/wp-includes/css/dist/block-library/style.min.css?ver=5.7.1' media='all' /> | |
| <link rel='stylesheet' id='wp-block-library-theme-css' href='https://www.benthamsgaze.org/wp-includes/css/dist/block-library/theme.min.css?ver=5.7.1' media='all' /> | |
| <link rel='stylesheet' id='parent-style-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/style.css?ver=5.7.1' media='all' /> | |
| <link rel='stylesheet' id='twentyfifteen-fonts-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen-child/fonts.css' media='all' /> | |
| <link rel='stylesheet' id='genericons-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/genericons/genericons.css?ver=20201208' media='all' /> | |
| <link rel='stylesheet' id='twentyfifteen-style-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen-child/style.css?ver=20201208' media='all' /> | |
| <style id='twentyfifteen-style-inline-css'> | |
| /* Color Scheme */ | |
| /* Background Color */ | |
| body { | |
| background-color: #e9f2f9; | |
| } | |
| /* Sidebar Background Color */ | |
| body:before, | |
| .site-header { | |
| background-color: #55c3dc; | |
| } | |
| /* Box Background Color */ | |
| .post-navigation, | |
| .pagination, | |
| .secondary, | |
| .site-footer, | |
| .hentry, | |
| .page-header, | |
| .page-content, | |
| .comments-area, | |
| .widecolumn { | |
| background-color: #ffffff; | |
| } | |
| /* Box Background Color */ | |
| button, | |
| input[type="button"], | |
| input[type="reset"], | |
| input[type="submit"], | |
| .pagination .prev, | |
| .pagination .next, | |
| .widget_calendar tbody a, | |
| .widget_calendar tbody a:hover, | |
| .widget_calendar tbody a:focus, | |
| .page-links a, | |
| .page-links a:hover, | |
| .page-links a:focus, | |
| .sticky-post { | |
| color: #ffffff; | |
| } | |
| /* Main Text Color */ | |
| button, | |
| input[type="button"], | |
| input[type="reset"], | |
| input[type="submit"], | |
| .pagination .prev, | |
| .pagination .next, | |
| .widget_calendar tbody a, | |
| .page-links a, | |
| .sticky-post { | |
| background-color: #22313f; | |
| } | |
| /* Main Text Color */ | |
| body, | |
| blockquote cite, | |
| blockquote small, | |
| a, | |
| .dropdown-toggle:after, | |
| .image-navigation a:hover, | |
| .image-navigation a:focus, | |
| .comment-navigation a:hover, | |
| .comment-navigation a:focus, | |
| .widget-title, | |
| .entry-footer a:hover, | |
| .entry-footer a:focus, | |
| .comment-metadata a:hover, | |
| .comment-metadata a:focus, | |
| .pingback .edit-link a:hover, | |
| .pingback .edit-link a:focus, | |
| .comment-list .reply a:hover, | |
| .comment-list .reply a:focus, | |
| .site-info a:hover, | |
| .site-info a:focus { | |
| color: #22313f; | |
| } | |
| /* Main Text Color */ | |
| .entry-content a, | |
| .entry-summary a, | |
| .page-content a, | |
| .comment-content a, | |
| .pingback .comment-body > a, | |
| .author-description a, | |
| .taxonomy-description a, | |
| .textwidget a, | |
| .entry-footer a:hover, | |
| .comment-metadata a:hover, | |
| .pingback .edit-link a:hover, | |
| .comment-list .reply a:hover, | |
| .site-info a:hover { | |
| border-color: #22313f; | |
| } | |
| /* Secondary Text Color */ | |
| button:hover, | |
| button:focus, | |
| input[type="button"]:hover, | |
| input[type="button"]:focus, | |
| input[type="reset"]:hover, | |
| input[type="reset"]:focus, | |
| input[type="submit"]:hover, | |
| input[type="submit"]:focus, | |
| .pagination .prev:hover, | |
| .pagination .prev:focus, | |
| .pagination .next:hover, | |
| .pagination .next:focus, | |
| .widget_calendar tbody a:hover, | |
| .widget_calendar tbody a:focus, | |
| .page-links a:hover, | |
| .page-links a:focus { | |
| background-color: #22313f; /* Fallback for IE7 and IE8 */ | |
| background-color: rgba( 34, 49, 63, 0.7); | |
| } | |
| /* Secondary Text Color */ | |
| blockquote, | |
| a:hover, | |
| a:focus, | |
| .main-navigation .menu-item-description, | |
| .post-navigation .meta-nav, | |
| .post-navigation a:hover .post-title, | |
| .post-navigation a:focus .post-title, | |
| .image-navigation, | |
| .image-navigation a, | |
| .comment-navigation, | |
| .comment-navigation a, | |
| .widget, | |
| .author-heading, | |
| .entry-footer, | |
| .entry-footer a, | |
| .taxonomy-description, | |
| .page-links > .page-links-title, | |
| .entry-caption, | |
| .comment-author, | |
| .comment-metadata, | |
| .comment-metadata a, | |
| .pingback .edit-link, | |
| .pingback .edit-link a, | |
| .post-password-form label, | |
| .comment-form label, | |
| .comment-notes, | |
| .comment-awaiting-moderation, | |
| .logged-in-as, | |
| .form-allowed-tags, | |
| .no-comments, | |
| .site-info, | |
| .site-info a, | |
| .wp-caption-text, | |
| .gallery-caption, | |
| .comment-list .reply a, | |
| .widecolumn label, | |
| .widecolumn .mu_register label { | |
| color: #22313f; /* Fallback for IE7 and IE8 */ | |
| color: rgba( 34, 49, 63, 0.7); | |
| } | |
| /* Secondary Text Color */ | |
| blockquote, | |
| .logged-in-as a:hover, | |
| .comment-author a:hover { | |
| border-color: #22313f; /* Fallback for IE7 and IE8 */ | |
| border-color: rgba( 34, 49, 63, 0.7); | |
| } | |
| /* Border Color */ | |
| hr, | |
| .dropdown-toggle:hover, | |
| .dropdown-toggle:focus { | |
| background-color: #22313f; /* Fallback for IE7 and IE8 */ | |
| background-color: rgba( 34, 49, 63, 0.1); | |
| } | |
| /* Border Color */ | |
| pre, | |
| abbr[title], | |
| table, | |
| th, | |
| td, | |
| input, | |
| textarea, | |
| .main-navigation ul, | |
| .main-navigation li, | |
| .post-navigation, | |
| .post-navigation div + div, | |
| .pagination, | |
| .comment-navigation, | |
| .widget li, | |
| .widget_categories .children, | |
| .widget_nav_menu .sub-menu, | |
| .widget_pages .children, | |
| .site-header, | |
| .site-footer, | |
| .hentry + .hentry, | |
| .author-info, | |
| .entry-content .page-links a, | |
| .page-links > span, | |
| .page-header, | |
| .comments-area, | |
| .comment-list + .comment-respond, | |
| .comment-list article, | |
| .comment-list .pingback, | |
| .comment-list .trackback, | |
| .comment-list .reply a, | |
| .no-comments { | |
| border-color: #22313f; /* Fallback for IE7 and IE8 */ | |
| border-color: rgba( 34, 49, 63, 0.1); | |
| } | |
| /* Border Focus Color */ | |
| a:focus, | |
| button:focus, | |
| input:focus { | |
| outline-color: #22313f; /* Fallback for IE7 and IE8 */ | |
| outline-color: rgba( 34, 49, 63, 0.3); | |
| } | |
| input:focus, | |
| textarea:focus { | |
| border-color: #22313f; /* Fallback for IE7 and IE8 */ | |
| border-color: rgba( 34, 49, 63, 0.3); | |
| } | |
| /* Sidebar Link Color */ | |
| .secondary-toggle:before { | |
| color: #ffffff; | |
| } | |
| .site-title a, | |
| .site-description { | |
| color: #ffffff; | |
| } | |
| /* Sidebar Text Color */ | |
| .site-title a:hover, | |
| .site-title a:focus { | |
| color: rgba( 255, 255, 255, 0.7); | |
| } | |
| /* Sidebar Border Color */ | |
| .secondary-toggle { | |
| border-color: #ffffff; /* Fallback for IE7 and IE8 */ | |
| border-color: rgba( 255, 255, 255, 0.1); | |
| } | |
| /* Sidebar Border Focus Color */ | |
| .secondary-toggle:hover, | |
| .secondary-toggle:focus { | |
| border-color: #ffffff; /* Fallback for IE7 and IE8 */ | |
| border-color: rgba( 255, 255, 255, 0.3); | |
| } | |
| .site-title a { | |
| outline-color: #ffffff; /* Fallback for IE7 and IE8 */ | |
| outline-color: rgba( 255, 255, 255, 0.3); | |
| } | |
| /* Meta Background Color */ | |
| .entry-footer { | |
| background-color: #f1f1f1; | |
| } | |
| @media screen and (min-width: 38.75em) { | |
| /* Main Text Color */ | |
| .page-header { | |
| border-color: #22313f; | |
| } | |
| } | |
| @media screen and (min-width: 59.6875em) { | |
| /* Make sure its transparent on desktop */ | |
| .site-header, | |
| .secondary { | |
| background-color: transparent; | |
| } | |
| /* Sidebar Background Color */ | |
| .widget button, | |
| .widget input[type="button"], | |
| .widget input[type="reset"], | |
| .widget input[type="submit"], | |
| .widget_calendar tbody a, | |
| .widget_calendar tbody a:hover, | |
| .widget_calendar tbody a:focus { | |
| color: #55c3dc; | |
| } | |
| /* Sidebar Link Color */ | |
| .secondary a, | |
| .dropdown-toggle:after, | |
| .widget-title, | |
| .widget blockquote cite, | |
| .widget blockquote small { | |
| color: #ffffff; | |
| } | |
| .widget button, | |
| .widget input[type="button"], | |
| .widget input[type="reset"], | |
| .widget input[type="submit"], | |
| .widget_calendar tbody a { | |
| background-color: #ffffff; | |
| } | |
| .textwidget a { | |
| border-color: #ffffff; | |
| } | |
| /* Sidebar Text Color */ | |
| .secondary a:hover, | |
| .secondary a:focus, | |
| .main-navigation .menu-item-description, | |
| .widget, | |
| .widget blockquote, | |
| .widget .wp-caption-text, | |
| .widget .gallery-caption { | |
| color: rgba( 255, 255, 255, 0.7); | |
| } | |
| .widget button:hover, | |
| .widget button:focus, | |
| .widget input[type="button"]:hover, | |
| .widget input[type="button"]:focus, | |
| .widget input[type="reset"]:hover, | |
| .widget input[type="reset"]:focus, | |
| .widget input[type="submit"]:hover, | |
| .widget input[type="submit"]:focus, | |
| .widget_calendar tbody a:hover, | |
| .widget_calendar tbody a:focus { | |
| background-color: rgba( 255, 255, 255, 0.7); | |
| } | |
| .widget blockquote { | |
| border-color: rgba( 255, 255, 255, 0.7); | |
| } | |
| /* Sidebar Border Color */ | |
| .main-navigation ul, | |
| .main-navigation li, | |
| .widget input, | |
| .widget textarea, | |
| .widget table, | |
| .widget th, | |
| .widget td, | |
| .widget pre, | |
| .widget li, | |
| .widget_categories .children, | |
| .widget_nav_menu .sub-menu, | |
| .widget_pages .children, | |
| .widget abbr[title] { | |
| border-color: rgba( 255, 255, 255, 0.1); | |
| } | |
| .dropdown-toggle:hover, | |
| .dropdown-toggle:focus, | |
| .widget hr { | |
| background-color: rgba( 255, 255, 255, 0.1); | |
| } | |
| .widget input:focus, | |
| .widget textarea:focus { | |
| border-color: rgba( 255, 255, 255, 0.3); | |
| } | |
| .sidebar a:focus, | |
| .dropdown-toggle:focus { | |
| outline-color: rgba( 255, 255, 255, 0.3); | |
| } | |
| } | |
| </style> | |
| <link rel='stylesheet' id='twentyfifteen-block-style-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/css/blocks.css?ver=20190102' media='all' /> | |
| <!--[if lt IE 9]> | |
| <link rel='stylesheet' id='twentyfifteen-ie-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/css/ie.css?ver=20170916' media='all' /> | |
| <![endif]--> | |
| <!--[if lt IE 8]> | |
| <link rel='stylesheet' id='twentyfifteen-ie7-css' href='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/css/ie7.css?ver=20141210' media='all' /> | |
| <![endif]--> | |
| <script src='https://www.benthamsgaze.org/wp-includes/js/jquery/jquery.min.js?ver=3.5.1' id='jquery-core-js'></script> | |
| <script src='https://www.benthamsgaze.org/wp-includes/js/jquery/jquery-migrate.min.js?ver=3.3.2' id='jquery-migrate-js'></script> | |
| <link rel="https://api.w.org/" href="https://www.benthamsgaze.org/wp-json/" /><link rel="alternate" type="application/json" href="https://www.benthamsgaze.org/wp-json/wp/v2/posts/1057" /><link rel="EditURI" type="application/rsd+xml" title="RSD" href="https://www.benthamsgaze.org/xmlrpc.php?rsd" /> | |
| <link rel="wlwmanifest" type="application/wlwmanifest+xml" href="https://www.benthamsgaze.org/wp-includes/wlwmanifest.xml" /> | |
| <meta name="generator" content="WordPress 5.7.1" /> | |
| <link rel="canonical" href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/" /> | |
| <link rel='shortlink' href='https://www.benthamsgaze.org/?p=1057' /> | |
| <link rel="alternate" type="application/json+oembed" href="https://www.benthamsgaze.org/wp-json/oembed/1.0/embed?url=https%3A%2F%2Fwww.benthamsgaze.org%2F2016%2F08%2F02%2Fdo-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack%2F" /> | |
| <link rel="alternate" type="text/xml+oembed" href="https://www.benthamsgaze.org/wp-json/oembed/1.0/embed?url=https%3A%2F%2Fwww.benthamsgaze.org%2F2016%2F08%2F02%2Fdo-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack%2F&format=xml" /> | |
| <meta name="referrer" content="no-referrer" /> | |
| <meta name="google-site-verification" content="bXJbar9cdv8SB0s_UZLmxtebUTcR-F11thJMbdjwtVg" /> | |
| <style>.recentcomments a{display:inline !important;padding:0 !important;margin:0 !important;}</style> <style type="text/css" id="twentyfifteen-header-css"> | |
| .site-header { | |
| /* | |
| * No shorthand so the Customizer can override individual properties. | |
| * @see https://core.trac.wordpress.org/ticket/31460 | |
| */ | |
| background-image: url(https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg); | |
| background-repeat: no-repeat; | |
| background-position: 50% 50%; | |
| -webkit-background-size: cover; | |
| -moz-background-size: cover; | |
| -o-background-size: cover; | |
| background-size: cover; | |
| } | |
| @media screen and (min-width: 59.6875em) { | |
| body:before { | |
| /* | |
| * No shorthand so the Customizer can override individual properties. | |
| * @see https://core.trac.wordpress.org/ticket/31460 | |
| */ | |
| background-image: url(https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg); | |
| background-repeat: no-repeat; | |
| background-position: 100% 50%; | |
| -webkit-background-size: cover; | |
| -moz-background-size: cover; | |
| -o-background-size: cover; | |
| background-size: cover; | |
| border-right: 0; | |
| } | |
| .site-header { | |
| background: transparent; | |
| } | |
| } | |
| </style> | |
| <!-- START - Open Graph and Twitter Card Tags 3.1.1 --> | |
| <!-- Facebook Open Graph --> | |
| <meta property="og:locale" content="en_GB"/> | |
| <meta property="og:site_name" content="Bentham’s Gaze"/> | |
| <meta property="og:title" content="Do you know what you're paying for? How contactless cards are still vulnerable to relay attack"/> | |
| <meta property="og:url" content="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/"/> | |
| <meta property="og:type" content="article"/> | |
| <meta property="og:description" content="Contactless card payments are fast and convenient, but convenience comes at a price: they are vulnerable to fraud. Some of these vulnerabilities are unique to contactless payment cards, and others are shared with the Chip and PIN cards – those that must be plugged into a card reader – upon which the"/> | |
| <meta property="og:image" content="https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg"/> | |
| <meta property="og:image:url" content="https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg"/> | |
| <meta property="og:image:secure_url" content="https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg"/> | |
| <meta property="article:published_time" content="2016-08-02T20:39:21+00:00"/> | |
| <meta property="article:modified_time" content="2016-08-24T12:56:35+00:00" /> | |
| <meta property="og:updated_time" content="2016-08-24T12:56:35+00:00" /> | |
| <meta property="article:section" content="Authentication"/> | |
| <meta property="article:section" content="Banking security"/> | |
| <meta property="article:section" content="Cryptography"/> | |
| <meta property="article:section" content="Mobile"/> | |
| <meta property="article:section" content="The Conversation"/> | |
| <meta property="article:author" content="https://www.facebook.com/sjmurdoch"/> | |
| <meta property="article:publisher" content="https://www.facebook.com/uclmscisec/"/> | |
| <!-- Google+ / Schema.org --> | |
| <meta itemprop="name" content="Do you know what you're paying for? How contactless cards are still vulnerable to relay attack"/> | |
| <meta itemprop="headline" content="Do you know what you're paying for? How contactless cards are still vulnerable to relay attack"/> | |
| <meta itemprop="description" content="Contactless card payments are fast and convenient, but convenience comes at a price: they are vulnerable to fraud. Some of these vulnerabilities are unique to contactless payment cards, and others are shared with the Chip and PIN cards – those that must be plugged into a card reader – upon which the"/> | |
| <meta itemprop="image" content="https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg"/> | |
| <meta itemprop="datePublished" content="2016-08-02"/> | |
| <meta itemprop="dateModified" content="2016-08-24T12:56:35+00:00" /> | |
| <meta itemprop="author" content="Steven J. Murdoch"/> | |
| <!--<meta itemprop="publisher" content="Bentham’s Gaze"/>--> <!-- To solve: The attribute publisher.itemtype has an invalid value --> | |
| <!-- Twitter Cards --> | |
| <meta name="twitter:title" content="Do you know what you're paying for? How contactless cards are still vulnerable to relay attack"/> | |
| <meta name="twitter:url" content="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/"/> | |
| <meta name="twitter:description" content="Contactless card payments are fast and convenient, but convenience comes at a price: they are vulnerable to fraud. Some of these vulnerabilities are unique to contactless payment cards, and others are shared with the Chip and PIN cards – those that must be plugged into a card reader – upon which the"/> | |
| <meta name="twitter:image" content="https://www.benthamsgaze.org/wp-content/uploads/2015/03/UCL_Night3-lg.jpg"/> | |
| <meta name="twitter:card" content="summary_large_image"/> | |
| <meta name="twitter:creator" content="@sjmurdoch"/> | |
| <meta name="twitter:site" content="@uclisec"/> | |
| <!-- SEO --> | |
| <meta name="description" content="Contactless card payments are fast and convenient, but convenience comes at a price: they are vulnerable to fraud. Some of these vulnerabilities are unique to contactless payment cards, and others are shared with the Chip and PIN cards – those that must be plugged into a card reader – upon which the"/> | |
| <meta name="author" content="Steven J. Murdoch"/> | |
| <meta name="publisher" content="Bentham’s Gaze"/> | |
| <!-- Misc. tags --> | |
| <!-- is_singular --> | |
| <!-- END - Open Graph and Twitter Card Tags 3.1.1 --> | |
| </head> | |
| <body class="post-template-default single single-post postid-1057 single-format-standard wp-embed-responsive"> | |
| <div id="page" class="hfeed site"> | |
| <a class="skip-link screen-reader-text" href="#content">Skip to content</a> | |
| <div id="sidebar" class="sidebar"> | |
| <header id="masthead" class="site-header" role="banner"> | |
| <div class="site-branding"> | |
| <p class="site-title"><a href="https://www.benthamsgaze.org/" rel="home">Bentham’s Gaze</a></p> | |
| <p class="site-description">Information Security Research & Education, University College London (UCL)</p> | |
| <button class="secondary-toggle">Menu and widgets</button> | |
| </div><!-- .site-branding --> | |
| </header><!-- .site-header --> | |
| <div id="secondary" class="secondary"> | |
| <nav id="site-navigation" class="main-navigation" role="navigation"> | |
| <div class="menu-top-menu-container"><ul id="menu-top-menu" class="nav-menu"><li id="menu-item-6" class="menu-item menu-item-type-post_type menu-item-object-page menu-item-6"><a href="https://www.benthamsgaze.org/about/">About this site</a></li> | |
| <li id="menu-item-1529" class="menu-item menu-item-type-post_type menu-item-object-page menu-item-1529"><a href="https://www.benthamsgaze.org/subscribing-to-benthams-gaze/">Subscribing to Bentham’s Gaze</a></li> | |
| <li id="menu-item-9" class="menu-item menu-item-type-custom menu-item-object-custom menu-item-9"><a href="http://sec.cs.ucl.ac.uk/">Information Security Research Group @ UCL</a></li> | |
| <li id="menu-item-10" class="menu-item menu-item-type-custom menu-item-object-custom menu-item-10"><a href="http://sec.cs.ucl.ac.uk/ace_csr/">ACE-CSR @ UCL</a></li> | |
| <li id="menu-item-51" class="menu-item menu-item-type-custom menu-item-object-custom menu-item-51"><a href="http://www.cs.ucl.ac.uk/prospective_students/msc_information_security/">MSc Information Security</a></li> | |
| <li id="menu-item-56" class="menu-item menu-item-type-post_type menu-item-object-page menu-item-56"><a href="https://www.benthamsgaze.org/contribution-policy/">Contribution policy</a></li> | |
| <li id="menu-item-2306" class="menu-item menu-item-type-post_type menu-item-object-page menu-item-privacy-policy menu-item-2306"><a href="https://www.benthamsgaze.org/privacy-policy/">Privacy Policy</a></li> | |
| </ul></div> </nav><!-- .main-navigation --> | |
| <nav id="social-navigation" class="social-navigation" role="navigation"> | |
| <div class="menu-social-links-container"><ul id="menu-social-links" class="menu"><li id="menu-item-230" class="menu-item menu-item-type-custom menu-item-object-custom menu-item-230"><a href="https://twitter.com/uclisec"><span class="screen-reader-text">Follow us on Twitter</span></a></li> | |
| <li id="menu-item-231" class="menu-item menu-item-type-custom menu-item-object-custom menu-item-231"><a href="https://www.facebook.com/uclmscisec/"><span class="screen-reader-text">Follow us on Facebook</span></a></li> | |
| <li id="menu-item-232" class="menu-item menu-item-type-custom menu-item-object-custom menu-item-232"><a href="https://www.linkedin.com/grp/home?gid=8207869"><span class="screen-reader-text">Follow us on LinkedIn</span></a></li> | |
| </ul></div> </nav><!-- .social-navigation --> | |
| <div id="widget-area" class="widget-area" role="complementary"> | |
| <aside id="search-2" class="widget widget_search"><form role="search" method="get" class="search-form" action="https://www.benthamsgaze.org/"> | |
| <label> | |
| <span class="screen-reader-text">Search for:</span> | |
| <input type="search" class="search-field" placeholder="Search …" value="" name="s" /> | |
| </label> | |
| <input type="submit" class="search-submit screen-reader-text" value="Search" /> | |
| </form></aside> | |
| <aside id="recent-posts-2" class="widget widget_recent_entries"> | |
| <h2 class="widget-title">Recent Posts</h2><nav role="navigation" aria-label="Recent Posts"> | |
| <ul> | |
| <li> | |
| <a href="https://www.benthamsgaze.org/2021/04/27/evidence-critical-systems-designing-for-dispute-resolution/">Evidence Critical Systems: Designing for Dispute Resolution</a> | |
| </li> | |
| <li> | |
| <a href="https://www.benthamsgaze.org/2021/03/24/aggregatable-distributed-key-generation/">Aggregatable Distributed Key Generation</a> | |
| </li> | |
| <li> | |
| <a href="https://www.benthamsgaze.org/2021/03/16/still-treating-users-as-the-enemy-entrapment-and-the-escalating-nastiness-of-simulated-phishing-campaigns/">Still treating users as the enemy: entrapment and the escalating nastiness of simulated phishing campaigns</a> | |
| </li> | |
| <li> | |
| <a href="https://www.benthamsgaze.org/2020/10/16/thoughts-on-the-future-implications-of-microsofts-legal-approach-towards-the-trickbot-takedown/">Thoughts on the Future Implications of Microsoft’s Legal Approach towards the TrickBot Takedown</a> | |
| </li> | |
| <li> | |
| <a href="https://www.benthamsgaze.org/2020/09/16/winkle-a-decentralised-checkpointing-for-proof-of-stake/">Winkle – Decentralised Checkpointing for Proof-of-Stake</a> | |
| </li> | |
| </ul> | |
| </nav></aside><aside id="calendar-2" class="widget widget_calendar"><div id="calendar_wrap" class="calendar_wrap"><table id="wp-calendar" class="wp-calendar-table"> | |
| <caption>August 2016</caption> | |
| <thead> | |
| <tr> | |
| <th scope="col" title="Monday">M</th> | |
| <th scope="col" title="Tuesday">T</th> | |
| <th scope="col" title="Wednesday">W</th> | |
| <th scope="col" title="Thursday">T</th> | |
| <th scope="col" title="Friday">F</th> | |
| <th scope="col" title="Saturday">S</th> | |
| <th scope="col" title="Sunday">S</th> | |
| </tr> | |
| </thead> | |
| <tbody> | |
| <tr><td>1</td><td><a href="https://www.benthamsgaze.org/2016/08/02/" aria-label="Posts published on 2 August 2016">2</a></td><td>3</td><td>4</td><td><a href="https://www.benthamsgaze.org/2016/08/05/" aria-label="Posts published on 5 August 2016">5</a></td><td>6</td><td>7</td> | |
| </tr> | |
| <tr> | |
| <td>8</td><td>9</td><td>10</td><td>11</td><td>12</td><td>13</td><td>14</td> | |
| </tr> | |
| <tr> | |
| <td>15</td><td>16</td><td>17</td><td>18</td><td>19</td><td>20</td><td>21</td> | |
| </tr> | |
| <tr> | |
| <td>22</td><td><a href="https://www.benthamsgaze.org/2016/08/23/" aria-label="Posts published on 23 August 2016">23</a></td><td>24</td><td>25</td><td>26</td><td>27</td><td>28</td> | |
| </tr> | |
| <tr> | |
| <td>29</td><td>30</td><td>31</td> | |
| <td class="pad" colspan="4"> </td> | |
| </tr> | |
| </tbody> | |
| </table><nav aria-label="Previous and next months" class="wp-calendar-nav"> | |
| <span class="wp-calendar-nav-prev"><a href="https://www.benthamsgaze.org/2016/07/">« Jul</a></span> | |
| <span class="pad"> </span> | |
| <span class="wp-calendar-nav-next"><a href="https://www.benthamsgaze.org/2016/09/">Sep »</a></span> | |
| </nav></div></aside><aside id="archives-2" class="widget widget_archive"><h2 class="widget-title">Archives</h2><nav role="navigation" aria-label="Archives"> | |
| <ul> | |
| <li><a href='https://www.benthamsgaze.org/2021/04/'>April 2021</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2021/03/'>March 2021</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2020/10/'>October 2020</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2020/09/'>September 2020</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2020/06/'>June 2020</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2020/04/'>April 2020</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2020/01/'>January 2020</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/12/'>December 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/11/'>November 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/10/'>October 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/09/'>September 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/08/'>August 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/07/'>July 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/06/'>June 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/05/'>May 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/04/'>April 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/03/'>March 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/02/'>February 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2019/01/'>January 2019</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/12/'>December 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/11/'>November 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/10/'>October 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/09/'>September 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/08/'>August 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/07/'>July 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/06/'>June 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/05/'>May 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/04/'>April 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/03/'>March 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/02/'>February 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2018/01/'>January 2018</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/12/'>December 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/11/'>November 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/10/'>October 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/08/'>August 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/07/'>July 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/06/'>June 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/05/'>May 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/04/'>April 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/03/'>March 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/02/'>February 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2017/01/'>January 2017</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/12/'>December 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/11/'>November 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/10/'>October 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/09/'>September 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/08/'>August 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/07/'>July 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/06/'>June 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/05/'>May 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/04/'>April 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/03/'>March 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/02/'>February 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2016/01/'>January 2016</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/12/'>December 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/11/'>November 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/10/'>October 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/09/'>September 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/08/'>August 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/07/'>July 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/06/'>June 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/05/'>May 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/04/'>April 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/03/'>March 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/02/'>February 2015</a></li> | |
| <li><a href='https://www.benthamsgaze.org/2015/01/'>January 2015</a></li> | |
| </ul> | |
| </nav></aside><aside id="recent-comments-2" class="widget widget_recent_comments"><h2 class="widget-title">Recent Comments</h2><nav role="navigation" aria-label="Recent Comments"><ul id="recentcomments"><li class="recentcomments"><span class="comment-author-link">SenorFloppyNuts</span> on <a href="https://www.benthamsgaze.org/2016/11/16/a-longitudinal-measurement-study-of-4chans-politically-incorrect-forum-and-its-effect-on-the-web/#comment-277028">A Longitudinal Measurement Study of 4chan’s Politically Incorrect Forum and its Effect on the Web</a></li><li class="recentcomments"><span class="comment-author-link">janni</span> on <a href="https://www.benthamsgaze.org/2018/12/13/memes-are-taking-the-alt-rights-message-of-hate-mainstream/#comment-275462">Memes are taking the alt-right’s message of hate mainstream</a></li><li class="recentcomments"><span class="comment-author-link">Nicholas Bohm</span> on <a href="https://www.benthamsgaze.org/2021/04/27/evidence-critical-systems-designing-for-dispute-resolution/#comment-272926">Evidence Critical Systems: Designing for Dispute Resolution</a></li><li class="recentcomments"><span class="comment-author-link"><a href='https://murdoch.is/' rel='external nofollow ugc' class='url'>Steven J. Murdoch</a></span> on <a href="https://www.benthamsgaze.org/2021/04/27/evidence-critical-systems-designing-for-dispute-resolution/#comment-272808">Evidence Critical Systems: Designing for Dispute Resolution</a></li><li class="recentcomments"><span class="comment-author-link"><a href='https://murdoch.is/' rel='external nofollow ugc' class='url'>Steven J. Murdoch</a></span> on <a href="https://www.benthamsgaze.org/2021/04/27/evidence-critical-systems-designing-for-dispute-resolution/#comment-272804">Evidence Critical Systems: Designing for Dispute Resolution</a></li></ul></nav></aside><aside id="categories-2" class="widget widget_categories"><h2 class="widget-title">Categories</h2><nav role="navigation" aria-label="Categories"> | |
| <ul> | |
| <li class="cat-item cat-item-21"><a href="https://www.benthamsgaze.org/category/advertising/">Advertising</a> | |
| </li> | |
| <li class="cat-item cat-item-44"><a href="https://www.benthamsgaze.org/category/authentication/">Authentication</a> | |
| </li> | |
| <li class="cat-item cat-item-25"><a href="https://www.benthamsgaze.org/category/banking-security/">Banking security</a> | |
| </li> | |
| <li class="cat-item cat-item-48"><a href="https://www.benthamsgaze.org/category/biometrics/">Biometrics</a> | |
| </li> | |
| <li class="cat-item cat-item-112"><a href="https://www.benthamsgaze.org/category/blockchain/">Blockchain</a> | |
| </li> | |
| <li class="cat-item cat-item-15"><a href="https://www.benthamsgaze.org/category/censorship-resistance/">Censorship resistance</a> | |
| </li> | |
| <li class="cat-item cat-item-29"><a href="https://www.benthamsgaze.org/category/crime-science/">Crime science</a> | |
| </li> | |
| <li class="cat-item cat-item-39"><a href="https://www.benthamsgaze.org/category/cryptocurrencies/">Cryptocurrencies</a> | |
| </li> | |
| <li class="cat-item cat-item-28"><a href="https://www.benthamsgaze.org/category/cryptography/">Cryptography</a> | |
| </li> | |
| <li class="cat-item cat-item-38"><a href="https://www.benthamsgaze.org/category/cyber-crime/">Cyber crime</a> | |
| </li> | |
| <li class="cat-item cat-item-30"><a href="https://www.benthamsgaze.org/category/education/">Education</a> | |
| </li> | |
| <li class="cat-item cat-item-18"><a href="https://www.benthamsgaze.org/category/genomics/">Genomics</a> | |
| </li> | |
| <li class="cat-item cat-item-73"><a href="https://www.benthamsgaze.org/category/hardware/">Hardware</a> | |
| </li> | |
| <li class="cat-item cat-item-13"><a href="https://www.benthamsgaze.org/category/infosec/">InfoSec group</a> | |
| </li> | |
| <li class="cat-item cat-item-36"><a href="https://www.benthamsgaze.org/category/inside-infosec/">Inside Infosec</a> | |
| </li> | |
| <li class="cat-item cat-item-17"><a href="https://www.benthamsgaze.org/category/internet-security/">Internet security</a> | |
| </li> | |
| <li class="cat-item cat-item-16"><a href="https://www.benthamsgaze.org/category/law-enforcement/">Law enforcement</a> | |
| </li> | |
| <li class="cat-item cat-item-57"><a href="https://www.benthamsgaze.org/category/legal-issues/">Legal issues</a> | |
| </li> | |
| <li class="cat-item cat-item-37"><a href="https://www.benthamsgaze.org/category/malware/">Malware</a> | |
| </li> | |
| <li class="cat-item cat-item-24"><a href="https://www.benthamsgaze.org/category/measurement/">Measurement</a> | |
| </li> | |
| <li class="cat-item cat-item-11"><a href="https://www.benthamsgaze.org/category/meta/">Meta</a> | |
| </li> | |
| <li class="cat-item cat-item-33"><a href="https://www.benthamsgaze.org/category/mobile/">Mobile</a> | |
| </li> | |
| <li class="cat-item cat-item-35"><a href="https://www.benthamsgaze.org/category/modelling/">Modelling</a> | |
| </li> | |
| <li class="cat-item cat-item-66"><a href="https://www.benthamsgaze.org/category/networking/">Networking</a> | |
| </li> | |
| <li class="cat-item cat-item-98"><a href="https://www.benthamsgaze.org/category/operating-systems/">Operating systems</a> | |
| </li> | |
| <li class="cat-item cat-item-144"><a href="https://www.benthamsgaze.org/category/philosophy-of-science/">Philosophy of science</a> | |
| </li> | |
| <li class="cat-item cat-item-14"><a href="https://www.benthamsgaze.org/category/privacy/">Privacy</a> | |
| </li> | |
| <li class="cat-item cat-item-47"><a href="https://www.benthamsgaze.org/category/public-policy/">Public policy</a> | |
| </li> | |
| <li class="cat-item cat-item-43"><a href="https://www.benthamsgaze.org/category/research-projects/">Research projects</a> | |
| </li> | |
| <li class="cat-item cat-item-34"><a href="https://www.benthamsgaze.org/category/security-economics/">Security economics</a> | |
| </li> | |
| <li class="cat-item cat-item-42"><a href="https://www.benthamsgaze.org/category/security-usability/">Security usability</a> | |
| </li> | |
| <li class="cat-item cat-item-121"><a href="https://www.benthamsgaze.org/category/social-networks/">Social networks</a> | |
| </li> | |
| <li class="cat-item cat-item-19"><a href="https://www.benthamsgaze.org/category/talks-and-panels/">Talks and panels</a> | |
| </li> | |
| <li class="cat-item cat-item-45"><a href="https://www.benthamsgaze.org/category/the-conversation/">The Conversation</a> | |
| </li> | |
| <li class="cat-item cat-item-67"><a href="https://www.benthamsgaze.org/category/voting/">Voting</a> | |
| </li> | |
| </ul> | |
| </nav></aside><aside id="meta-2" class="widget widget_meta"><h2 class="widget-title">Meta</h2><nav role="navigation" aria-label="Meta"> | |
| <ul> | |
| <li><a href="https://www.benthamsgaze.org/wp-login.php">Log in</a></li> | |
| <li><a href="https://www.benthamsgaze.org/feed/">Entries feed</a></li> | |
| <li><a href="https://www.benthamsgaze.org/comments/feed/">Comments feed</a></li> | |
| </ul> | |
| </nav></aside> </div><!-- .widget-area --> | |
| </div><!-- .secondary --> | |
| </div><!-- .sidebar --> | |
| <div id="content" class="site-content"> | |
| <div id="primary" class="content-area"> | |
| <main id="main" class="site-main" role="main"> | |
| <article id="post-1057" class="post-1057 post type-post status-publish format-standard hentry category-authentication category-banking-security category-cryptography category-mobile category-the-conversation"> | |
| <header class="entry-header"> | |
| <h1 class="entry-title">Do you know what you’re paying for? How contactless cards are still vulnerable to relay attack</h1> </header><!-- .entry-header --> | |
| <div class="entry-content"> | |
| <p>Contactless card payments are fast and convenient, but convenience comes at a price: they are vulnerable to fraud. Some of these vulnerabilities are unique to contactless payment cards, and others are shared with the Chip and PIN cards – those that must be plugged into a card reader – upon which they’re based. Both are vulnerable to what’s called a <a href="http://sec.cs.ucl.ac.uk/users/smurdoch/talks/ccc07relayattacks.pdf">relay attack</a>. The risk for contactless cards, however, is far higher because no PIN number is required to complete the transaction. Consequently, the card payments industry has been working on ways to solve this problem.</p> | |
| <p>The relay attack is also known as the “chess grandmaster attack”, by analogy to the <a href="http://en.chessbase.com/post/the-magical-che-experiment">ruse</a> in which someone who doesn’t know how to play chess can beat an expert: the player simultaneously challenges two grandmasters to an online game of chess, and uses the moves chosen by the first grandmaster in the game against the second grandmaster, and vice versa. By relaying the opponents’ moves between the games, the player appears to be a formidable opponent to both grandmasters, and will win (or at least force a draw) in one match.</p> | |
| <p>Similarly, in a relay attack the fraudster’s fake card doesn’t know how to respond properly to the payment terminal because, unlike a genuine card, it doesn’t contain the cryptographic key known only to the card and the bank that verifies the card is genuine. But like the fake chess grandmaster, the fraudster can relay the communication of the genuine card in place of the fake card.</p> | |
| <p>For example, the victim’s card (Alice, in the diagram below) would be in a fake or hacked card payment terminal (Bob) and the criminal would use the fake card (Carol) to attempt a purchase in a genuine terminal (Dave). The bank would challenge the fake card to prove its identity, this challenge is then relayed to the genuine card in the hacked terminal, and the genuine card’s response is relayed back on behalf of the fake card to the bank for verification. The end result is that the terminal used for the real purchase sees the fake card as genuine, and the victim later finds an unexpected and expensive purchase on their statement.</p> | |
| <figure id="attachment_1059" aria-describedby="caption-attachment-1059" style="width: 754px" class="wp-caption aligncenter"><img loading="lazy" src="https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-17177-12o458d.png" alt="A rigged payment terminal capable of performing the relay attack can be made from off-the-shelf components" width="754" height="328" class="size-full wp-image-1059" srcset="https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-17177-12o458d.png 754w, https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-17177-12o458d-300x131.png 300w" sizes="(max-width: 754px) 100vw, 754px" /><figcaption id="caption-attachment-1059" class="wp-caption-text">The relay attack, where the cards and terminals can be at any distance from each other</figcaption></figure> | |
| <h2>Demonstrating the grandmaster attack</h2> | |
| <p>I first demonstrated that this vulnerability was real with my colleague <a href="http://www.saardrimer.com/sd410/">Saar Drimer</a> at Cambridge, showing on television how the attack could work <a href="https://www.youtube.com/watch?v=X7pjUIxKoEc">in Britain in 2007</a> and <a href="https://vimeo.com/8241248">in the Netherlands in 2009</a>.</p> | |
| <p>In our scenario, the victim put their card in a fake terminal thinking they were buying a coffee when in fact their card details were relayed by a radio link to another shop, where the criminal used a fake card to buy something far more expensive. The fake terminal showed the victim only the price of a cup of coffee, but when the bank statement arrives later the victim has an unpleasant surprise.</p> | |
| <p><iframe loading="lazy" width="660" height="371" src="https://www.youtube-nocookie.com/embed/X7pjUIxKoEc" frameborder="0" allowfullscreen></iframe></p> | |
| <p>At the time, the banking industry agreed that the vulnerability was real, but argued that as it was difficult to carry out in practice <a href="https://www.finextra.com/news/fullstory.aspx?newsitemid=16466">it was not a serious risk</a>. It’s true that, to avoid suspicion, the fraudulent purchase must take place within a few tens of seconds of the victim putting their card into the fake terminal. But this restriction only applies to the Chip and PIN contact cards available at the time. The same vulnerability applies to today’s contactless cards, only now the fraudster need only be physically near the victim at the time – contactless cards can communicate at a distance, even while the card is in the victim’s pocket or bag.</p> | |
| <p><span id="more-1057"></span>While we had to build hardware ourselves (from off-the-shelf components) to demonstrate the relay attack, today it can be carried out with any modern smartphone equipped with <a href="http://www.techradar.com/news/phone-and-communications/what-is-nfc-and-why-is-it-in-your-phone-948410">near-field communication chips</a>, which can read or imitate contactless cards. All a criminal needs is <a href="https://eprint.iacr.org/2011/618.pdf">two cheap smartphones and some software</a> – which could be sold on the black market, if it is not already available. This change is likely the reason why, years after our demonstration, the industry has developed a defence against the relay attack, but only for contactless cards.</p> | |
| <figure id="attachment_1063" aria-describedby="caption-attachment-1063" style="width: 660px" class="wp-caption aligncenter"><img loading="lazy" src="https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-428-1e8u9u8-1024x550.png" alt="A rigged payment terminal capable of performing the relay attack can be made from off-the-shelf components." width="660" height="354" class="size-large wp-image-1063" srcset="https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-428-1e8u9u8-1024x550.png 1024w, https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-428-1e8u9u8-300x161.png 300w, https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-428-1e8u9u8-768x412.png 768w, https://www.benthamsgaze.org/wp-content/uploads/2016/08/image-20160802-428-1e8u9u8.png 1615w" sizes="(max-width: 660px) 100vw, 660px" /><figcaption id="caption-attachment-1063" class="wp-caption-text">A rigged payment terminal capable of performing the relay attack can be made from off-the-shelf components</figcaption></figure> | |
| <h2>Closing the loophole</h2> | |
| <p>The industry’s defence is <a href="http://www.cl.cam.ac.uk/research/security/banking/relay/">based on a design</a> that Saar and I developed at the same time that we demonstrated the vulnerability, called distance bounding. When the terminal challenges the card to prove its identity, it measures how long the card takes to respond. During a genuine transaction there should be very little delay, but a fake card will take longer to respond because it is relaying the response of the genuine card, located much further away. The terminal will notice this delay, and cancel the transaction.</p> | |
| <p>We set the maximum delay to 20 nanoseconds – the time it takes a radio signal to travel six metres; this would guarantee the genuine card is no further away than this from the terminal. However, the contactless card designers made some compromises in order to be compatible with the hundreds of thousands of terminals already in use, which allows far less precise timing. The <a href="http://www.emvco.com/download_agreement.aspx?id=1238">new, updated card specification</a> sets the maximum delay the terminal allows at two milliseconds: that’s two million nanoseconds, during which a radio signal could travel 600 kilometres.</p> | |
| <p>The reason that the timing constraints of the new contactless card standard are much less precise than our prototype is that the new contactless cards’ distance bounding exchange uses the same (relatively slow) communication protocol as the rest of the transaction. In our design, the distance bounding exchange uses a special high-speed mode. Also, the new contactless cards send a single 32-bit challenge and expect a 32-bit response, whereas in our prototype there is a repeated single-bit challenge and single-bit response (based on a protocol by <a href="https://www.cl.cam.ac.uk/~mgk25/sc2005-distance.pdf">Hancke and Kuhn</a>). For both of these reasons, in our prototype, compared to the new contactless cards, each challenge-response exchange is far more rapid and hence the timing can be much more precise.</p> | |
| <p>Clearly this doesn’t offer the same guarantees as our design, but it would still represent a substantial obstacle to criminals. While it’s enough time for the radio signal to travel far, it’s still a very short window for the software to process the transaction. When we demonstrated the relay attack it regularly introduced delays of hundreds or even thousands of milliseconds. A relay attack against contactless cards using off-the-shelf components <a href="https://www.blackhat.com/docs/asia-15/materials/asia-15-VandenBreekel-Relaying-EMV-Contactless-Transactions-Using-Off-The-Shelf-Android-Devices-wp.pdf">would be similar</a>.</p> | |
| <p>It will be years before the new secure cards reach customers, and even then only some: there is only one Chip and PIN specification, but there are <a href="https://pomcor.com/2014/09/20/apple-pay-must-be-using-the-mag-stripe-mode-of-the-emv-contactless-specifications/">seven specifications for contactless cards</a>, and only the MasterCard variant includes this defence. It’s not perfect, but it makes pragmatic compromises that should prevent smartphones being used by fraudsters as tools for the relay attack. The sort of custom-designed hardware that could still defeat this protection would require expertise and expense to build – and the banks will hope that they can stay ahead of the criminals until the arrival of whatever replaces contactless cards in the future.</p> | |
| <p> </p> | |
| <p><em>An edited version of this article was originally published on <a href="https://theconversation.com/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack-63142">The Conversation</a>, written by <a href="http://theconversation.com/profiles/steven-j-murdoch-152093">Steven J. Murdoch</a>, <a href="http://theconversation.com/institutions/ucl">UCL</a>.<img loading="lazy" alt="The Conversation" height="1" src="https://counter.theconversation.edu.au/content/63142/count.gif" width="1" /></em></p> | |
| </div><!-- .entry-content --> | |
| <footer class="entry-footer"> | |
| <span class="posted-on"><span class="screen-reader-text">Posted on </span><a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/" rel="bookmark"><time class="entry-date published" datetime="2016-08-02T20:39:21+00:00">2016-08-02</time><time class="updated" datetime="2016-08-24T12:56:35+00:00">2016-08-24</time></a></span><span class="byline"><span class="author vcard"><span class="screen-reader-text">Author </span><a href="https://www.benthamsgaze.org/author/smurdoch/" title="Posts by Steven J. Murdoch" class="author url fn" rel="author">Steven J. Murdoch</a></span></span><span class="cat-links"><span class="screen-reader-text">Categories </span><a href="https://www.benthamsgaze.org/category/authentication/" rel="category tag">Authentication</a>, <a href="https://www.benthamsgaze.org/category/banking-security/" rel="category tag">Banking security</a>, <a href="https://www.benthamsgaze.org/category/cryptography/" rel="category tag">Cryptography</a>, <a href="https://www.benthamsgaze.org/category/mobile/" rel="category tag">Mobile</a>, <a href="https://www.benthamsgaze.org/category/the-conversation/" rel="category tag">The Conversation</a></span> </footer><!-- .entry-footer --> | |
| </article><!-- #post-1057 --> | |
| <div id="comments" class="comments-area"> | |
| <h2 class="comments-title"> | |
| 8 thoughts on “Do you know what you’re paying for? How contactless cards are still vulnerable to relay attack” </h2> | |
| <ol class="comment-list"> | |
| <li id="comment-35231" class="comment even thread-even depth-1 parent"> | |
| <article id="div-comment-35231" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/9779090bfb7bb108f40bdd341eaba95a?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/9779090bfb7bb108f40bdd341eaba95a?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn"><a href='https://github.com/nfcgate/nfcgate' rel='external nofollow ugc' class='url'>Max</a></b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-35231"><time datetime="2016-08-04T15:17:54+00:00">2016-08-04 at 15:17 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>Hey Steven, just wanted to let you know that we wrote an Android app for NFC relay attacks that’ll run on a modern smartphone (e.g. Nexus 5) and will also fake the UID of the card, and we made it open source. See <a href="https://github.com/nfcgate/nfcgate" rel="nofollow ugc">https://github.com/nfcgate/nfcgate</a> for details. Maybe it’ll be helpful for you or someone else reading the article. </p> | |
| <p>Also, I’m glad to see that this hole is being closed now, albeit slowly. Some systems we tested are vulnerable and will not be getting fixes :(.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=35231#respond' data-commentid="35231" data-postid="1057" data-belowelement="div-comment-35231" data-respondelement="respond" data-replyto="Reply to Max" aria-label='Reply to Max'>Reply</a></div> </article><!-- .comment-body --> | |
| <ol class="children"> | |
| <li id="comment-35330" class="comment byuser comment-author-smurdoch bypostauthor odd alt depth-2 parent"> | |
| <article id="div-comment-35330" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/1a8ce462a151b76e544a5f3d7981d608?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/1a8ce462a151b76e544a5f3d7981d608?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn"><a href='http://sec.cs.ucl.ac.uk/users/smurdoch/' rel='external nofollow ugc' class='url'>Steven J. Murdoch</a></b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-35330"><time datetime="2016-08-05T09:45:53+00:00">2016-08-05 at 09:45 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>@Max,</p> | |
| <p>Thanks for your comment. It is good to confirm that indeed the software needed is out there.</p> | |
| <p>Did you measure the delay introduced by your software? I would be curious to know how much this is in reality.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=35330#respond' data-commentid="35330" data-postid="1057" data-belowelement="div-comment-35330" data-respondelement="respond" data-replyto="Reply to Steven J. Murdoch" aria-label='Reply to Steven J. Murdoch'>Reply</a></div> </article><!-- .comment-body --> | |
| <ol class="children"> | |
| <li id="comment-35344" class="comment even depth-3"> | |
| <article id="div-comment-35344" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/9779090bfb7bb108f40bdd341eaba95a?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/9779090bfb7bb108f40bdd341eaba95a?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn"><a href='https://github.com/nfcgate/nfcgate' rel='external nofollow ugc' class='url'>Max</a></b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-35344"><time datetime="2016-08-05T13:20:55+00:00">2016-08-05 at 13:20 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>We did a brief measurement, and ended up with 65 +-38 ms of delay in a local WiFi (See the <a href="https://blog.velcommuta.de/wp-content/uploads/2015/07/nfcgate-extended-abstract.pdf" rel="nofollow">extended abstract</a> and <a href="https://blog.velcommuta.de/wp-content/uploads/2015/07/NFCGate-Poster.pdf" rel="nofollow">poster</a> linked in the GitHub Readme). That is mostly due to the fact that we have a client-server infrastructure (Reader Android 1 Server Android 2 Card), which is not very optimized. You could probably lower that latency with direct connections and more efficient code, but obviously not below practical distance bounding limits – it’s a proof of concept and not designed to bypass distance bounding.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=35344#respond' data-commentid="35344" data-postid="1057" data-belowelement="div-comment-35344" data-respondelement="respond" data-replyto="Reply to Max" aria-label='Reply to Max'>Reply</a></div> </article><!-- .comment-body --> | |
| </li><!-- #comment-## --> | |
| </ol><!-- .children --> | |
| </li><!-- #comment-## --> | |
| </ol><!-- .children --> | |
| </li><!-- #comment-## --> | |
| <li id="comment-35257" class="comment odd alt thread-odd thread-alt depth-1 parent"> | |
| <article id="div-comment-35257" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/01868f9dadc966a293cfc6567e14a7b9?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/01868f9dadc966a293cfc6567e14a7b9?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn">Jan Ciger</b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-35257"><time datetime="2016-08-04T19:12:40+00:00">2016-08-04 at 19:12 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>There is also a second mitigation strategy banks and shops use – the contactless payment is restricted to something like 20 EUR and you can do only 3 or so in a row. After that the terminal will refuse the transaction and demand a normal payment using chip & pin instead. </p> | |
| <p>So while this doesn’t prevent the attack, it significantly limits the possible impact – in this case to max 60 EUR. Still nasty, but nowhere close to the much higher limits when a regular chip & pin transaction is done.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=35257#respond' data-commentid="35257" data-postid="1057" data-belowelement="div-comment-35257" data-respondelement="respond" data-replyto="Reply to Jan Ciger" aria-label='Reply to Jan Ciger'>Reply</a></div> </article><!-- .comment-body --> | |
| <ol class="children"> | |
| <li id="comment-35334" class="comment byuser comment-author-smurdoch bypostauthor even depth-2"> | |
| <article id="div-comment-35334" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/1a8ce462a151b76e544a5f3d7981d608?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/1a8ce462a151b76e544a5f3d7981d608?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn"><a href='http://sec.cs.ucl.ac.uk/users/smurdoch/' rel='external nofollow ugc' class='url'>Steven J. Murdoch</a></b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-35334"><time datetime="2016-08-05T10:41:07+00:00">2016-08-05 at 10:41 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>@Jan</p> | |
| <p>Indeed, transaction limits still apply. In the UK this is £30 per transaction (and there can be a request to enter a PIN periodically, but this has never happened to me). </p> | |
| <p>This mitigates the risk, though there is also the possibility that the limits <a href="http://www.ncl.ac.uk/press/news/legacy/2014/11/contactlesscardsfailtorecogniseforeigncurrency.html" rel="nofollow">could be bypassed</a>.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=35334#respond' data-commentid="35334" data-postid="1057" data-belowelement="div-comment-35334" data-respondelement="respond" data-replyto="Reply to Steven J. Murdoch" aria-label='Reply to Steven J. Murdoch'>Reply</a></div> </article><!-- .comment-body --> | |
| </li><!-- #comment-## --> | |
| </ol><!-- .children --> | |
| </li><!-- #comment-## --> | |
| <li id="comment-76941" class="comment odd alt thread-even depth-1 parent"> | |
| <article id="div-comment-76941" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/f8ae58fe8ae7745b87cc524d5ace3265?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/f8ae58fe8ae7745b87cc524d5ace3265?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn">Alexandre Marinkovic</b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-76941"><time datetime="2017-09-18T22:19:45+00:00">2017-09-18 at 22:19 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>Al this is considering that the payment terminal has been opened without activating the tampering detection which can be done an old terminal as on the video but quite impossible on recently PCI certified device.<br /> | |
| The devices when opened are erasing the encrypted key which are allowing them to communicate with the bank. they become useless, especially for the demonstration described in this article.<br /> | |
| Nowadays the terminals are well secured but I agree that there are multiple skimmer integration attempts , especially on ATMs with fake keyboard or plates, including cameras, all for capturing the PIN and then it is not the responsibility of the cardholder, I think , if the PIN is stolen.. No we have the PIN on Glass coming soon , which will authorized the PIN to be entered on any phone who’s able to read a contactless credit card and process the transaction, I am becoming really concerned .. especially that a Phone is fully accessible anytime to hackers ( a payment terminal is not by the way) ..</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=76941#respond' data-commentid="76941" data-postid="1057" data-belowelement="div-comment-76941" data-respondelement="respond" data-replyto="Reply to Alexandre Marinkovic" aria-label='Reply to Alexandre Marinkovic'>Reply</a></div> </article><!-- .comment-body --> | |
| <ol class="children"> | |
| <li id="comment-77195" class="comment byuser comment-author-smurdoch bypostauthor even depth-2"> | |
| <article id="div-comment-77195" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/1a8ce462a151b76e544a5f3d7981d608?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/1a8ce462a151b76e544a5f3d7981d608?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn"><a href='http://sec.cs.ucl.ac.uk/users/smurdoch/' rel='external nofollow ugc' class='url'>Steven J. Murdoch</a></b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-77195"><time datetime="2017-09-21T14:49:17+00:00">2017-09-21 at 14:49 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>The relay attack doesn’t require evading the tamper-resistance measures because the terminal that the victim interacts with never communicates with the bank. The modified terminal is there to trick the customer into presenting their card (and potentially PIN) so only has to <strong>look</strong> plausible – the electronics inside can be replaced entirely. PCI security standards only requires that tampering be detectable by the bank, not the customer.</p> | |
| <p>For example, here’s a Verifone SC5000 terminal that we’ve been experimenting with. It’s PCI certified but we were easily able to open it and remove the internals. It has a standard display module which we could connect to replacement electronics. With the addition of a NFC antenna and contactless payment sticker, I’m confident customers would use it without hesitation.</p> | |
| <p><img src="https://www.benthamsgaze.org/wp-content/uploads/2017/09/IMG_3489.jpg" width="660" /></p> | |
| <p>The question of customer liability is a different issue. The approach of the UK banks has been that if a PIN is used for a transaction then the customer must have been negligent and hence liable for the fraud. It would be for the customer to show that the PIN was obtained through skimming, which is extremely difficult. We need <a href="https://www.benthamsgaze.org/2017/05/03/online-security-wont-improve-until-companies-stop-passing-the-buck-to-the-customer/">changes to regulation</a> to reverse this unfair situation. </p> | |
| <p>It will indeed be interesting to see what will happen with the relaxing of PCI standards to allow PIN-on-glass. Provided that there is robust regulation that ensures risks are not systemic and that customers don’t pay the cost of fraud, I would welcome careful experimentation in this area.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=77195#respond' data-commentid="77195" data-postid="1057" data-belowelement="div-comment-77195" data-respondelement="respond" data-replyto="Reply to Steven J. Murdoch" aria-label='Reply to Steven J. Murdoch'>Reply</a></div> </article><!-- .comment-body --> | |
| </li><!-- #comment-## --> | |
| </ol><!-- .children --> | |
| </li><!-- #comment-## --> | |
| <li id="comment-82830" class="comment odd alt thread-odd thread-alt depth-1"> | |
| <article id="div-comment-82830" class="comment-body"> | |
| <footer class="comment-meta"> | |
| <div class="comment-author vcard"> | |
| <img alt='' src='https://secure.gravatar.com/avatar/4298396fc037fccc7ed0673fe41817e6?s=56&d=mm&r=g' srcset='https://secure.gravatar.com/avatar/4298396fc037fccc7ed0673fe41817e6?s=112&d=mm&r=g 2x' class='avatar avatar-56 photo' height='56' width='56' loading='lazy'/> <b class="fn">Matthew Gaunt</b> <span class="says">says:</span> </div><!-- .comment-author --> | |
| <div class="comment-metadata"> | |
| <a href="https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#comment-82830"><time datetime="2018-01-12T13:47:46+00:00">2018-01-12 at 13:47 UTC</time></a> </div><!-- .comment-metadata --> | |
| </footer><!-- .comment-meta --> | |
| <div class="comment-content"> | |
| <p>Hi Steven,</p> | |
| <p>I notice that Mastercard have taken measures to address this with the “Relay Resistance Protocol” in M/Chip Advance.</p> | |
| <p>Perhaps they read your blog…</p> | |
| <p>Cheers, M.</p> | |
| </div><!-- .comment-content --> | |
| <div class="reply"><a rel='nofollow' class='comment-reply-link' href='https://www.benthamsgaze.org/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/?replytocom=82830#respond' data-commentid="82830" data-postid="1057" data-belowelement="div-comment-82830" data-respondelement="respond" data-replyto="Reply to Matthew Gaunt" aria-label='Reply to Matthew Gaunt'>Reply</a></div> </article><!-- .comment-body --> | |
| </li><!-- #comment-## --> | |
| </ol><!-- .comment-list --> | |
| <div id="respond" class="comment-respond"> | |
| <h3 id="reply-title" class="comment-reply-title">Leave a Reply <small><a rel="nofollow" id="cancel-comment-reply-link" href="/2016/08/02/do-you-know-what-youre-paying-for-how-contactless-cards-are-still-vulnerable-to-relay-attack/#respond" style="display:none;">Cancel reply</a></small></h3><form action="https://www.benthamsgaze.org/wp-comments-post.php" method="post" id="commentform" class="comment-form" novalidate><p class="comment-notes"><span id="email-notes">Your email address will not be published.</span> Required fields are marked <span class="required">*</span></p><p class="comment-form-comment"><label for="comment">Comment</label> <textarea id="comment" name="comment" cols="45" rows="8" maxlength="65525" required="required"></textarea></p><p class="comment-form-author"><label for="author">Name <span class="required">*</span></label> <input id="author" name="author" type="text" value="" size="30" maxlength="245" required='required' /></p> | |
| <p class="comment-form-email"><label for="email">Email <span class="required">*</span></label> <input id="email" name="email" type="email" value="" size="30" maxlength="100" aria-describedby="email-notes" required='required' /></p> | |
| <p class="comment-form-url"><label for="url">Website</label> <input id="url" name="url" type="url" value="" size="30" maxlength="200" /></p> | |
| <p class="form-submit"><input name="submit" type="submit" id="submit" class="submit" value="Post Comment" /> <input type='hidden' name='comment_post_ID' value='1057' id='comment_post_ID' /> | |
| <input type='hidden' name='comment_parent' id='comment_parent' value='0' /> | |
| </p><p style="display: none;"><input type="hidden" id="akismet_comment_nonce" name="akismet_comment_nonce" value="9d4a771650" /></p><input type="hidden" id="ak_js" name="ak_js" value="221"/><textarea name="ak_hp_textarea" cols="45" rows="8" maxlength="100" style="display: none !important;"></textarea></form> </div><!-- #respond --> | |
| </div><!-- .comments-area --> | |
| <nav class="navigation post-navigation" role="navigation" aria-label="Posts"> | |
| <h2 class="screen-reader-text">Post navigation</h2> | |
| <div class="nav-links"><div class="nav-previous"><a href="https://www.benthamsgaze.org/2016/07/29/analyzing-privacy-aspects-of-the-w3c-vibration-api/" rel="prev"><span class="meta-nav" aria-hidden="true">Previous</span> <span class="screen-reader-text">Previous post:</span> <span class="post-title">Analyzing privacy aspects of the W3C Vibration API</span></a></div><div class="nav-next"><a href="https://www.benthamsgaze.org/2016/08/05/moving-towards-security-and-privacy-experiments-for-the-real-world/" rel="next"><span class="meta-nav" aria-hidden="true">Next</span> <span class="screen-reader-text">Next post:</span> <span class="post-title">Moving towards security and privacy experiments for the real world</span></a></div></div> | |
| </nav> | |
| </main><!-- .site-main --> | |
| </div><!-- .content-area --> | |
| </div><!-- .site-content --> | |
| <footer id="colophon" class="site-footer" role="contentinfo"> | |
| <div class="site-info"> | |
| <a class="privacy-policy-link" href="https://www.benthamsgaze.org/privacy-policy/">Privacy Policy</a><span role="separator" aria-hidden="true"></span> <a href="https://wordpress.org/" class="imprint"> | |
| Proudly powered by WordPress </a> | |
| </div><!-- .site-info --> | |
| </footer><!-- .site-footer --> | |
| </div><!-- .site --> | |
| <script src='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/js/skip-link-focus-fix.js?ver=20141028' id='twentyfifteen-skip-link-focus-fix-js'></script> | |
| <script src='https://www.benthamsgaze.org/wp-includes/js/comment-reply.min.js?ver=5.7.1' id='comment-reply-js'></script> | |
| <script id='twentyfifteen-script-js-extra'> | |
| var screenReaderText = {"expand":"<span class=\"screen-reader-text\">expand child menu<\/span>","collapse":"<span class=\"screen-reader-text\">collapse child menu<\/span>"}; | |
| </script> | |
| <script src='https://www.benthamsgaze.org/wp-content/themes/twentyfifteen/js/functions.js?ver=20171218' id='twentyfifteen-script-js'></script> | |
| <script src='https://www.benthamsgaze.org/wp-includes/js/wp-embed.min.js?ver=5.7.1' id='wp-embed-js'></script> | |
| <script async="async" src='https://www.benthamsgaze.org/wp-content/plugins/akismet/_inc/form.js?ver=4.1.9' id='akismet-form-js'></script> | |
| </body> | |
| </html> | |
Do you know what you’re paying for? How contactless cards are still vulnerable to relay attack
Contactless card payments are fast and convenient, but convenience comes at a price: they are vulnerable to fraud. Some of these vulnerabilities are unique to contactless payment cards, and others are shared with the Chip and PIN cards – those that must be plugged into a card reader – upon which they’re based. Both are vulnerable to what’s called a relay attack. The risk for contactless cards, however, is far higher because no PIN number is required to complete the transaction. Consequently, the card payments industry has been working on ways to solve this problem.
The relay attack is also known as the “chess grandmaster attack”, by analogy to the ruse in which someone who doesn’t know how to play chess can beat an expert: the player simultaneously challenges two grandmasters to an online game of chess, and uses the moves chosen by the first grandmaster in the game against the second grandmaster, and vice versa. By relaying the opponents’ moves between the games, the player appears to be a formidable opponent to both grandmasters, and will win (or at least force a draw) in one match.
Similarly, in a relay attack the fraudster’s fake card doesn’t know how to respond properly to the payment terminal because, unlike a genuine card, it doesn’t contain the cryptographic key known only to the card and the bank that verifies the card is genuine. But like the fake chess grandmaster, the fraudster can relay the communication of the genuine card in place of the fake card.
For example, the victim’s card (Alice, in the diagram below) would be in a fake or hacked card payment terminal (Bob) and the criminal would use the fake card (Carol) to attempt a purchase in a genuine terminal (Dave). The bank would challenge the fake card to prove its identity, this challenge is then relayed to the genuine card in the hacked terminal, and the genuine card’s response is relayed back on behalf of the fake card to the bank for verification. The end result is that the terminal used for the real purchase sees the fake card as genuine, and the victim later finds an unexpected and expensive purchase on their statement.
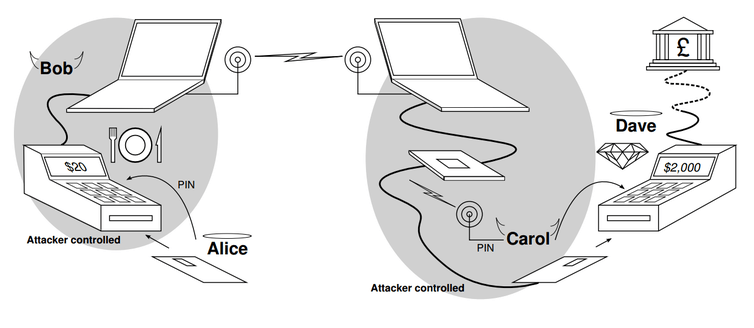
Demonstrating the grandmaster attack
I first demonstrated that this vulnerability was real with my colleague Saar Drimer at Cambridge, showing on television how the attack could work in Britain in 2007 and in the Netherlands in 2009.
In our scenario, the victim put their card in a fake terminal thinking they were buying a coffee when in fact their card details were relayed by a radio link to another shop, where the criminal used a fake card to buy something far more expensive. The fake terminal showed the victim only the price of a cup of coffee, but when the bank statement arrives later the victim has an unpleasant surprise.
At the time, the banking industry agreed that the vulnerability was real, but argued that as it was difficult to carry out in practice it was not a serious risk. It’s true that, to avoid suspicion, the fraudulent purchase must take place within a few tens of seconds of the victim putting their card into the fake terminal. But this restriction only applies to the Chip and PIN contact cards available at the time. The same vulnerability applies to today’s contactless cards, only now the fraudster need only be physically near the victim at the time – contactless cards can communicate at a distance, even while the card is in the victim’s pocket or bag.
While we had to build hardware ourselves (from off-the-shelf components) to demonstrate the relay attack, today it can be carried out with any modern smartphone equipped with near-field communication chips, which can read or imitate contactless cards. All a criminal needs is two cheap smartphones and some software – which could be sold on the black market, if it is not already available. This change is likely the reason why, years after our demonstration, the industry has developed a defence against the relay attack, but only for contactless cards.
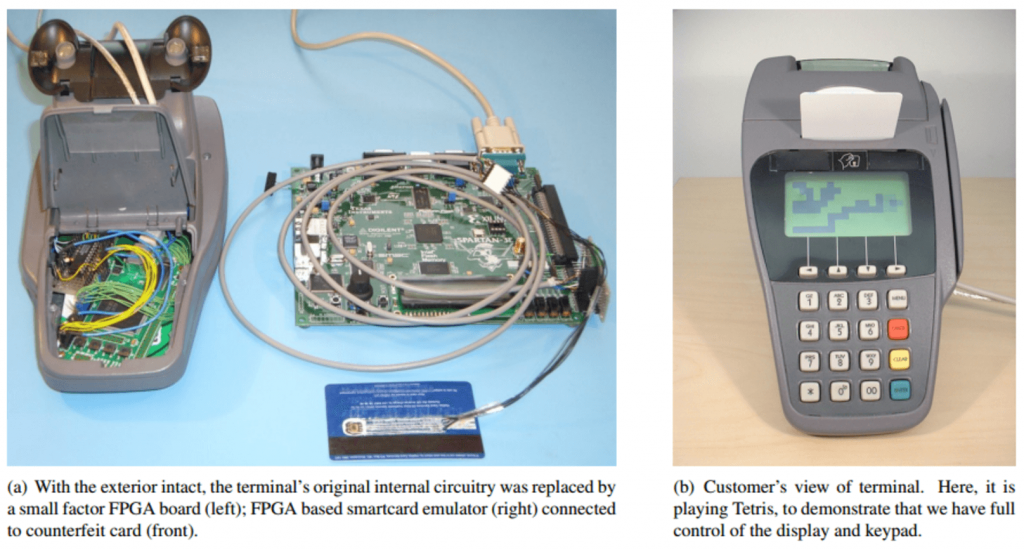
Closing the loophole
The industry’s defence is based on a design that Saar and I developed at the same time that we demonstrated the vulnerability, called distance bounding. When the terminal challenges the card to prove its identity, it measures how long the card takes to respond. During a genuine transaction there should be very little delay, but a fake card will take longer to respond because it is relaying the response of the genuine card, located much further away. The terminal will notice this delay, and cancel the transaction.
We set the maximum delay to 20 nanoseconds – the time it takes a radio signal to travel six metres; this would guarantee the genuine card is no further away than this from the terminal. However, the contactless card designers made some compromises in order to be compatible with the hundreds of thousands of terminals already in use, which allows far less precise timing. The new, updated card specification sets the maximum delay the terminal allows at two milliseconds: that’s two million nanoseconds, during which a radio signal could travel 600 kilometres.
The reason that the timing constraints of the new contactless card standard are much less precise than our prototype is that the new contactless cards’ distance bounding exchange uses the same (relatively slow) communication protocol as the rest of the transaction. In our design, the distance bounding exchange uses a special high-speed mode. Also, the new contactless cards send a single 32-bit challenge and expect a 32-bit response, whereas in our prototype there is a repeated single-bit challenge and single-bit response (based on a protocol by Hancke and Kuhn). For both of these reasons, in our prototype, compared to the new contactless cards, each challenge-response exchange is far more rapid and hence the timing can be much more precise.
Clearly this doesn’t offer the same guarantees as our design, but it would still represent a substantial obstacle to criminals. While it’s enough time for the radio signal to travel far, it’s still a very short window for the software to process the transaction. When we demonstrated the relay attack it regularly introduced delays of hundreds or even thousands of milliseconds. A relay attack against contactless cards using off-the-shelf components would be similar.
It will be years before the new secure cards reach customers, and even then only some: there is only one Chip and PIN specification, but there are seven specifications for contactless cards, and only the MasterCard variant includes this defence. It’s not perfect, but it makes pragmatic compromises that should prevent smartphones being used by fraudsters as tools for the relay attack. The sort of custom-designed hardware that could still defeat this protection would require expertise and expense to build – and the banks will hope that they can stay ahead of the criminals until the arrival of whatever replaces contactless cards in the future.
An edited version of this article was originally published on The Conversation, written by Steven J. Murdoch, UCL.![]()
Hey Steven, just wanted to let you know that we wrote an Android app for NFC relay attacks that’ll run on a modern smartphone (e.g. Nexus 5) and will also fake the UID of the card, and we made it open source. See https://github.com/nfcgate/nfcgate for details. Maybe it’ll be helpful for you or someone else reading the article.
Also, I’m glad to see that this hole is being closed now, albeit slowly. Some systems we tested are vulnerable and will not be getting fixes :(.
@Max,
Thanks for your comment. It is good to confirm that indeed the software needed is out there.
Did you measure the delay introduced by your software? I would be curious to know how much this is in reality.
We did a brief measurement, and ended up with 65 +-38 ms of delay in a local WiFi (See the extended abstract and poster linked in the GitHub Readme). That is mostly due to the fact that we have a client-server infrastructure (Reader Android 1 Server Android 2 Card), which is not very optimized. You could probably lower that latency with direct connections and more efficient code, but obviously not below practical distance bounding limits – it’s a proof of concept and not designed to bypass distance bounding.
There is also a second mitigation strategy banks and shops use – the contactless payment is restricted to something like 20 EUR and you can do only 3 or so in a row. After that the terminal will refuse the transaction and demand a normal payment using chip & pin instead.
So while this doesn’t prevent the attack, it significantly limits the possible impact – in this case to max 60 EUR. Still nasty, but nowhere close to the much higher limits when a regular chip & pin transaction is done.
@Jan
Indeed, transaction limits still apply. In the UK this is £30 per transaction (and there can be a request to enter a PIN periodically, but this has never happened to me).
This mitigates the risk, though there is also the possibility that the limits could be bypassed.
Al this is considering that the payment terminal has been opened without activating the tampering detection which can be done an old terminal as on the video but quite impossible on recently PCI certified device.
The devices when opened are erasing the encrypted key which are allowing them to communicate with the bank. they become useless, especially for the demonstration described in this article.
Nowadays the terminals are well secured but I agree that there are multiple skimmer integration attempts , especially on ATMs with fake keyboard or plates, including cameras, all for capturing the PIN and then it is not the responsibility of the cardholder, I think , if the PIN is stolen.. No we have the PIN on Glass coming soon , which will authorized the PIN to be entered on any phone who’s able to read a contactless credit card and process the transaction, I am becoming really concerned .. especially that a Phone is fully accessible anytime to hackers ( a payment terminal is not by the way) ..
The relay attack doesn’t require evading the tamper-resistance measures because the terminal that the victim interacts with never communicates with the bank. The modified terminal is there to trick the customer into presenting their card (and potentially PIN) so only has to look plausible – the electronics inside can be replaced entirely. PCI security standards only requires that tampering be detectable by the bank, not the customer.
For example, here’s a Verifone SC5000 terminal that we’ve been experimenting with. It’s PCI certified but we were easily able to open it and remove the internals. It has a standard display module which we could connect to replacement electronics. With the addition of a NFC antenna and contactless payment sticker, I’m confident customers would use it without hesitation.
The question of customer liability is a different issue. The approach of the UK banks has been that if a PIN is used for a transaction then the customer must have been negligent and hence liable for the fraud. It would be for the customer to show that the PIN was obtained through skimming, which is extremely difficult. We need changes to regulation to reverse this unfair situation.
It will indeed be interesting to see what will happen with the relaxing of PCI standards to allow PIN-on-glass. Provided that there is robust regulation that ensures risks are not systemic and that customers don’t pay the cost of fraud, I would welcome careful experimentation in this area.
Hi Steven,
I notice that Mastercard have taken measures to address this with the “Relay Resistance Protocol” in M/Chip Advance.
Perhaps they read your blog…
Cheers, M.